Rutuparna Rout • January 29, 2026
What is third party risk management (TPRM)? | A complete guide

Last update: February 5, 2026
Having multiple connections is great in any business setting, but it’s especially important when you’re a procurement leader and working with third-party vendors, suppliers, and local partners. It opens up more avenues for profit and gets you better product quality, but it doesn’t come without risks. Third party risk management helps companies protect themselves against these risks by helping them identify, assess, and control them. Catching these risks when they first pop up and controlling them is very important, as it protects the company’s relationships and reputation in the industry. This blog will tell you about why TPRM is essential, key risk factors to watch out for, best practices to ensure your processes are secure, and how AI-powered tools help you safeguard your sourcing process against all harm. Keep reading to learn more.
What is third party risk management, or TPRM?
Third party risk management (TPRM) is the structured process wherein a business identifies, assesses, controls, and mitigates risk that stems from working with external vendors, suppliers, or contractors. This process is managed by third parties that oversee critical tasks like IT services, supply chains, or customer data, which can expose businesses to many risks. These include security concerns, compliance issues, and operational risks. A TPRM process helps educate an organization on how third parties operate, the safeguards they use, and the risks they bring. It helps them stay updated on the aspects they should consider, what they should watch out for, and how they can protect themselves.
Why is third-party risk management important?
The sole function of third party risk management (TPRM) is to shield and protect organizations from harm that a number of factors can cause. Some of these can be external vendors, suppliers, or partners. These parties can knowingly or unknowingly harm a business with threats such as cyberattacks, data leaks, regulatory non-compliance, and risks that can damage their reputation. Implementing a strong and well-planned third party risk management program helps businesses stay secure and ensures that they remain compliant and protected against future threats.
Here are the key reasons why businesses need TPRM:
- Safety-proof their operations: This makes operations more resilient andprevents disruptions from vendor outages, supply chain issues, or service interruptions (e.g., cloud services going offline or delivery delays).
- Cybersecurity protection: This guards sensitive data from unauthorized third- and fourth-party access.
- Regulatory compliance: Meets rules like GDPR and CCPA to avoid fines.
- Cost and expertise benefits: Outsourcing saves money and taps external expertise, but unmanaged risks can be costly.
- Complexity reduction: Each third party adds vulnerabilities; TPRM solutions simplify oversight.
- Reputation management: Ensures vendors follow ethical and security standards.
Therefore, in businesses, a clear TPRM framework is necessary as it guides assessment, making a procurement audit easier, helps in monitoring, and mitigating risks.
What is a third party risk assessment?
A TPRM assessment is the process of identifying, analyzing, and reducing the risks an organization faces from its business relationships with external vendors, suppliers, and partners that a company relies on. Conducting these assessments ensures third parties don’t cause any issues in the procurement process. They analyze the risk of cyberthreats, data leaks, security breaches, or anything else that could harm a company’s reputation or its day-to-day operations.
You can think of these as planning for any damages and eliminating them, or at least trying to, before they become big problems. These assessments evaluate and categorize all potential risks from suppliers, service providers, consultants, partners, or any other connected entity. For example, consulting a marketing agency to improve SEO, a cloud hosting service, or an ESG consultant is all classified as third parties, as they are not directly involved with your company.
As part of the third-party risk management process, these assessments help organizations classify vendors by access and risk levels. However, not every third party needs the same amount of patrolling. This is more focused towards vendors who have direct access to sensitive data, like handling payments, as they carry a heavier risk than just office supply vendors.
Additionally, these assessments can be carried out in-house or by hiring independent contractors. The results guide organizations in creating a tailored third party risk management program, which gives businesses more insight and oversight and makes third-party relationships safe.
What are the components of the TPRM lifecycle?
The third-party risk management lifecycle is the step-by-step process organizations follow to manage risks from external vendors. A strong lifecycle ensures that all third-party relationships are secure, compliant, and mutually beneficial for all parties involved. The third party risk management program follows a structured framework, which includes planning, due diligence, risk monitoring and elimination, continuous optimization, and vendor offboarding and termination. This TPRM framework aims to manage risks before they arise and ensure the source-to-pay process runs as smoothly as possible.
1. Planning and vendor identification
The first step in the TPRM lifecycle is identifying all third parties, including current and potential vendors. This is where organizations gather all their vendor information from different sources. These can be from various places, like spreadsheets and contracts. You may even have to dive into your databases to find information. This helps build a full inventory of suppliers and their offers. Planning ensures that risks like shadow IT are minimized and sets a good base for the lifecycle.
2. Due diligence and selection
Before a company onboards its vendors, they need to be put through a series of evaluations to determine if they fit the company’s standards. This is done through things such as questionnaires, document reviews, and assessments. TPRM assessments are necessary to check their security and compliance, as well as how financially healthy they are. It also checks how reliable they are and how well they’re able to carry out operational duties. Proper due diligence ensures only reliable vendors are selected. Using TPRM software can automate data collection and simplify evaluations.
3. Onboarding and contracting
Onboarding formalizes and confirms the new partnership between the company and the supplier. Here’s where procurement contract management can help by introducing terms of confidentiality. It also includes the protection of company and supplier data and the services that both parties agree on. Lastly, contracting includes compliance rules and laws such as GDPR or HIPAA. Clear and previously agreed-upon policies and SLAs make things transparent and set expectations for everyone.
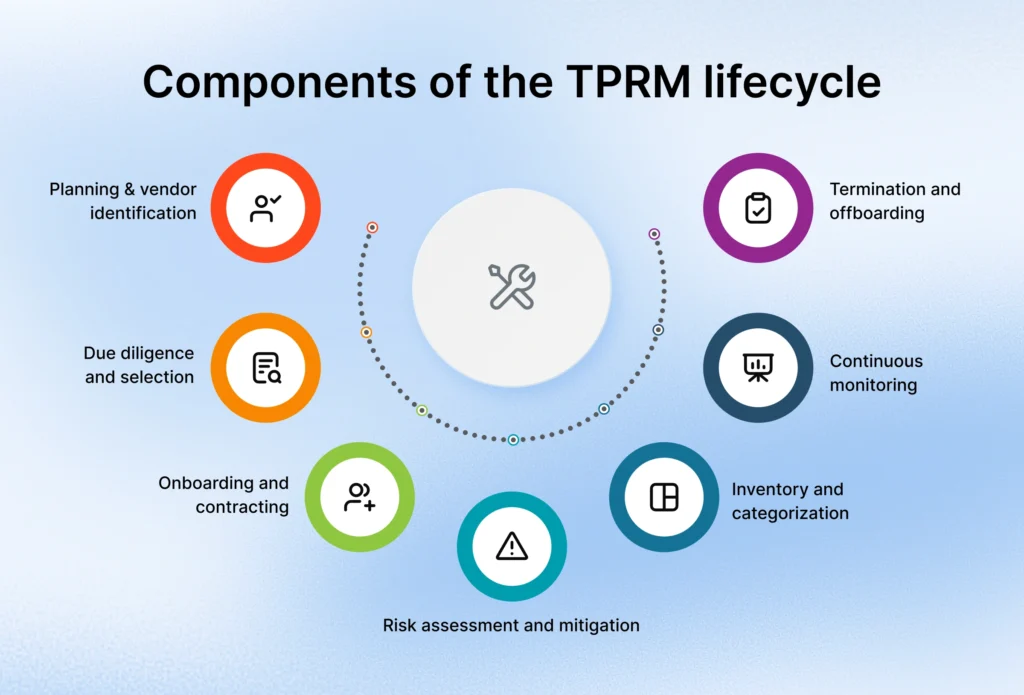
4. Risk assessment and mitigation
Vendors are assessed for all of the risks they could possibly pose. These include cybersecurity, financial, operational, and reputational risks. If an assessment finds a high-risk vendor, they may need to be replaced, or a multi-factor authentication system may need to be put in place. Continuously monitoring how vendors perform using TPRM tools can help track them and prevent breaches and data leaks.
5. Inventory and categorization
A detailed vendor inventory is maintained. Doing this helps in categorizing vendors by their risk level, and it also helps track their quotes and progress. This helps organizations turn their attention toward high-risk vendors and make the third-party risk management process more transparent.
6. Continuous monitoring
Vendor risks keep evolving. It’s up to companies to check and track any changes that may affect vendor performance and, ultimately, their own reputation. They track changes like regulatory updates, financial shifts, acquisitions, or unethical behaviour. Automated monitoring alerts in responding fast, before small risks turn into unmanageable breaches.
7. Termination and offboarding
The offboarding process ensures that the vendors don’t have access to any of the important company records, data is returned to the company or securely deleted, and compliance records are maintained. This final stage protects the organization from any risks that might remain after the term has ended with the third party.
So, why does the TPRM lifecycle matter so much?
The third-party risk management lifecycle is like a guidebook for company and vendor partnerships. It tells you exactly what you need to do and how to conduct operations. Not to mention, it reduces cyber risks, ensures you’re compliant, and protects your reputation. It also supports resilience in today’s world, where everything is interlinked, and where one vendor issue can affect the entire supply chain.
What are the most common third-party risks?
The most common third-party risks include cybersecurity, operational, compliance, reputational, financial, strategic, geopolitical, and ethical issues. These risks can cause data leaks, downtime, fines against the company, or even cause the company to stop all operations completely, depending on the severity of the risks. To solve these issues, strong third-party risk management solutions are essential. Here are these risks explained in detail.
1. Cybersecurity risk
If a vendor is hacked, it can expose your data or risk spreading attacks like ransomware. Taking the MOVEit breach in 2023 as an example of the severity of this risk, which caused massive data leaks all over the world. Cybersecurity risk is one of the biggest reasons companies use TPRM software.
2. Operational risk
If a vendor has problems, it automatically means that your business will be impacted as well. Examples include AWS outages that cause websites to be taken offline, or the Suez Canal blockage in 2021 that delayed supply chains.
3. Compliance & legal risk
Vendor assessments are very important to ensure that all of their activities stay in line with rules and laws. If a vendor doesn’t follow laws like GDPR, HIPAA, PCI DSS, or CCPA, your business could face fines or penalties. This can happen even if you didn’t know what the vendor was doing and were not at fault.
4. Financial risk
A vendor’s poor finances, bad pricing, or weak supply chain can impact your revenue negatively and cause significant losses. The COVID-19 pandemic is a good example of how quickly supplier issues can cause inventory backlogs and cash flow problems.
5. Strategic risk
This happens when vendor practices don’t match your goals. You could call it a conflict of interest, in casual terms. If your procurement strategy doesn’t align with how they operate, you may not agree on how to handle changes such as mergers, acquisitions, or market shifts. This can cause problems in communication and overall operations because you aren’t on the same page.
6. Reputational risk
Even if your systems are safe, a vendor’s failure can cause problems for you. A vendor’s shortcomings, like a security breach or unethical practice, can affect your brand and make customers lose trust in you.
7. Geopolitical risk
Vendors in unstable regions can cause problems. Sometimes, there can be sudden, uncontrollable situations that cause the economy to become unstable. These can be wars, sanctions, or even changes in rules. They can disrupt operations and affect the supply chain. Here, the issues seen during the Russia-Ukraine conflict can significantly impact business.
8. Ethical risk
Some vendors may break labor, safety, or environmental standards. And it’s more likely that instead of blaming the third party, your company will be blamed even if you didn’t cause it. This, of course, damages trust and reputation.
What are the best practices of the TPRM process?
When building a strong third party risk management program, it’s essential that you follow proven steps, as that lowers risks and keeps your operations safe. Some of the key TPRM best practices include setting clear goals, defining your risk appetite, doing proper due diligence, conducting risk assessments for all third parties, ensuring regulatory compliance, using automation, and preparing for unexpected events using continuous monitoring. Risks should be monitored using a TPRM lifecycle approach that includes onboarding and offboarding procedures. Therefore, when you approach your procure-to-pay process smartly, along with good third party risk management solutions, you can successfully protect your data while saving time and costs.
1. Define clear goals and policies
Start by setting clear risk appetite and goals. You should identify and segregate the different risks that can affect your operations, like cybersecurity, financial, compliance, operational, and reputational. Then, you need to decide what level of risk your organization can accept and what risk type definitely needs to be eliminated.
2. Involve all of your stakeholders
A TPRM process works its best if everyone knows what’s going on. And you never know, you can get new inputs and perspectives from knowledgeable people in your company. This is why it’s important to involve compliance, procurement, IT, security, and leadership teams from the start.
3. Build vendor inventories and tiering
Not all vendors carry the same risk. Group them into tiers like so:
- Tier 1 (High risk/critical) – vendors handling sensitive data, critical services, or big contracts. Suppliers in this tier need the most due diligence.
- Tier 2 (Medium risk/critical) – moderate data access or low service impact. This tier needs regular monitoring.
- Tier 3 (Low risk/critical) – little data access, like office supplies. Vendors in this category don’t need as much oversight as the others.
As a company, you should focus your attention more on the high-tier vendors.
4. Conduct vendor due diligence
Check vendors carefully before and during contracts. Look at their security practices, financial stability, compliance, and privacy safeguards. Not treating this stage as important can cost you later on, as you might miss red flags.
5. Use automation to save time and make processes faster
Instead of relying on slow, manual processes, automate tasks like onboarding vendors, sending reminders, scoring risks, and running reports. This makes the third-party risk management process faster and more reliable.
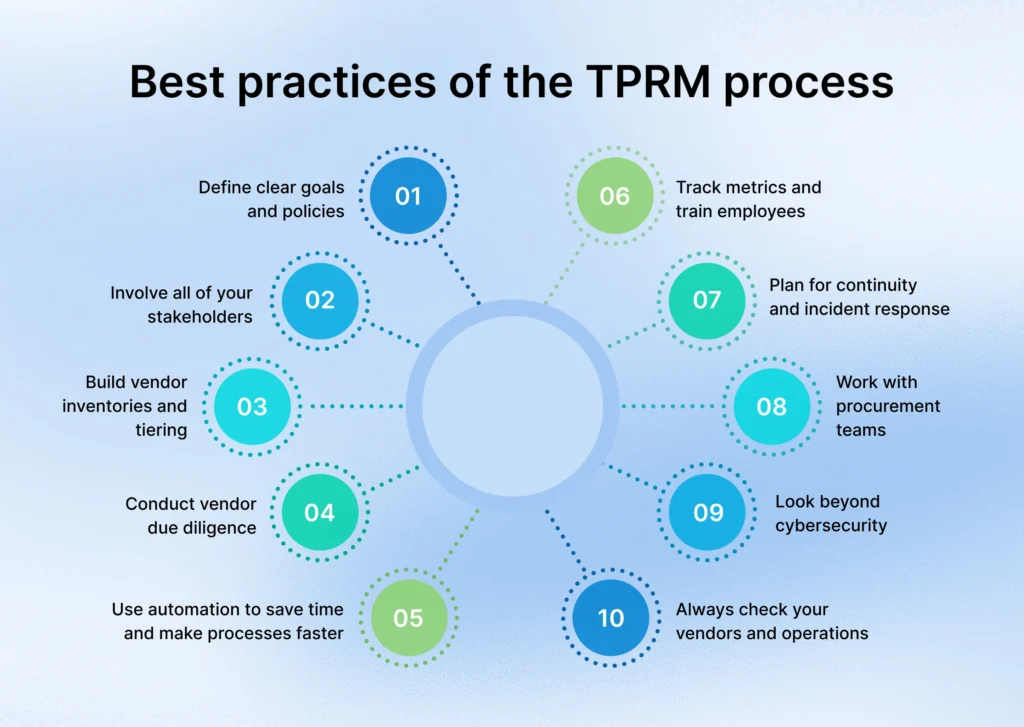
6. Always check your vendors and operations
Don’t just check vendors once. Instead, you should track them as often as possible. Here’s where you can use a procurement audit to help you monitor progress and detect any issues early. Third-party risk management solutions help you spot and eliminate risks like compliance failures or cyber threats.
7. Look beyond cybersecurity
Risks aren’t limited to the digital space. It’s best to keep an eye out for others, such as financial, geopolitical, ethical, reputational, environmental, and operational risks. You should also watch for concentration risk, which is the risk of relying on only one vendor.
8. Work with procurement teams
Procurement plays a big role in third party risk management. These teams can assess suppliers before contracts are signed and find any external risks that may be missed by others, like trade disputes or supply disruptions.
9. Plan for continuity and incident response
Just because you’ve had a good procurement negotiation discussion and terms have been agreed upon, doesn’t mean everything will go as planned. You must be ready for vendor failures or crises. Your third party risk management process should have continuity plans, disaster recovery steps, and incident response drills that your third parties are also aware of.
10. Track metrics and train employees
Use clear metrics to measure vendor performance and risks. As for your employees, it’s important to train them regularly so that they understand their role in managing third-party relationships.
What are the benefits of using third party risk management software?
Third-party risk management software offers benefits like security by identifying risks and vulnerabilities, improved efficiency through automation, cost savings with more streamlined processes, better compliance with regulations, gives better visibility for smarter decisions, and strengthens your supply chain and overall reputation. Here are the many benefits of using TPRM solutions, highlighted further.
1. Save your team time and reduce costs
One of the TPRM best practices includes reducing repetitive and manual tasks, such as spreadsheets and manual follow-ups. Digital tools come with automated alerts that help companies identify high-risk vendors, so teams can focus only on what matters. This saves money and avoids costly mistakes.
2. Protect data and stay compliant
A third-party risk management software ensures vendors follow rules like GDPR or HIPAA. Non-compliance can lead to fines, lawsuits, or lost customer trust. The software tracks and reports compliance automatically.
3. See all your vendor data in one place
Dashboards give real-time visibility of numerous aspects like vendor status, risk scores, and activities. This continuous tracking and consolidation of information helps you quickly see vendors handling sensitive data or those that failed recent assessments, which improves oversight.
4. Ensure vendors perform consistently
A third party risk management process monitors various procurement KPIs and SLA compliance to assess if vendors meet the company’s expectations. Checking helps identify problems that tend to pop up multiple times, so you can address them before they disrupt operations.
5. Strengthen customer trust
Third-party risk management software helps build trust between customers and vendors. It ensures that vendors follow rules set by your company, ultimately building confidence in their operations. Customers feel valued and secure knowing their information is in good hands.
6. Reduce financial and operational risks
Monitoring vendors often helps prevent many issues, especially financial losses, supply chain interruptions, or legal problems. Risk management software alerts you to risks that could possibly affect your operations or revenue.
7. Simplify reporting and audits
Automatic reports help leaders update statuses and approve or disapprove requests easily. They also help them conduct regular audits, as these reports have detailed information on where exactly the problem area is. This makes the process precise and therefore reduces errors and saves time. It also ensures that compliance evidence is always ready.
8. Scale your third party risk management program
Third-party risk management solutions aren’t left behind as your business grows. As you expand, it helps you add new vendors automatically and expand your risk management program. And even as operations get bigger, it keeps decision-making and risk management simple.
What are the TPRM trends in 2026?
In 2026, third-party risk management programs are becoming smarter and faster. The key trends for TPRM include companies being more reliant on AI for assessments and monitoring, more emphasis on cybersecurity, increased regulatory checks, especially around cloud and AI adoption, and a shift toward nth-party risk intelligence. Here’s a better explanation.
1. Growing use of AI in vendor risk management
AI is becoming more popular in the 2026 risk management world, as it helps complete third party risk assessments quickly. It’s also helpful in identifying and mapping supply chains and prioritizing and classifying risks. Additionally, it helps speed up vendor TPRM assessments, such as questionnaires and cross-check answers. However, AI automation can also bring risks like data leaks or wrong results.
2. Risks in AI and supply chains
AI isn’t completely risk-free. Third-party AI can affect data privacy, customer trust, and cybersecurity. As more suppliers turn toward AI, organizations must track all Nth parties and know their potential risks to stay safe.
3. Cloud-first strategies and data security
Companies shifting their operations to cloud platforms need strong controls. External or outsourced cloud services may not be the most dependable, as they can create gaps or inconsistencies in information, which is why it’s important to monitor access and configurations.
4. Stricter cybersecurity regulations
As governments around the world are introducing new rules like DORA, NYDFS, and NIS2, they require businesses to monitor vendors, perform regular risk checks, and create action plans. This ensures that operations are compliant and protect sensitive data.
5. Emerging AI regulations
Laws like the EU AI Act and California SB 1047 require the use of AI to be as safe, ethical, and transparent as possible. This automatically makes companies accountable and responsible for risks and makes testing for issues important before the deployment of AI tools.
6. Continuous monitoring and threat intelligence
Companies are becoming more vigilant about their operations and how well vendors are performing. This is where real-time monitoring of vendors, automated alerts, and threat intelligence helps. Companies can easily detect problems using third party risk management and avoid delays or disruptions.
7. Growing dependency on third parties
Companies are relying more on vendors for urgent and critical processes. Therefore, TPRM teams need more advanced and streamlined tools to track contracts and assess risks well. This helps companies manage multiple vendors easily and efficiently.
8. Advanced ICT tools for smarter risk management
New technologies like predictive analytics, blockchain, and smart contracts help businesses manage risks in multiple ways. They act like a company’s eyes and ears to spot risks early on and keep track of rules automatically. This helps in making third-party risk management faster and more reliable.
How Procol is the best third party risk management software
Procol makes managing vendors, suppliers, and partners simple and secure. With our third-party risk management software, you can see all your third parties in one place and track potential risks. With us, you can rest assured that your data is protected.
Our intuitive platform allows you to conduct fast and detailed third party risk assessments. Using AI-powered automation, you can identify financial, operational, or compliance issues before they start to hinder your procurement process. Our software allows you to eliminate risk areas as soon as they arise, so your activities can stay problem-free. Our system automates key tasks, such as vendor onboarding and offboarding. It also allows you to monitor vendor performance and rank their profiles based on the risk level, so your third-party risk management program is easier and gets the job done right to the last detail.
And we don’t just stick to basic security checks. Instead, we map third, fourth, and even nth-party relationships so that you can see hidden risks across the entire supply chain. We don’t just remove current risks; we also shield you from potential harm. Our customizable templates allow you to create clear, step-by-step plans to fix issues and improve vendor performance.
Our automated workflows keep things efficient, centralized data keeps processes organized, and continuous monitoring ensures you’re always secure and prepared, making Procol the best third party risk management software solution available today.

Conclusion
It’s not possible to manually check and keep track of all the risks lurking in your network. You could try, but things may fall through the cracks. When you use third party risk management, you’re not just keeping a checklist. Instead, you’re safeguarding yourself against things that could permanently damage your reputation, like data leaks, downtime, and security breaches. With smart TPRM tools, you can eliminate threats and stay compliant, keeping operations smooth and error-free. Remember to stay vigilant, take control, and use Procol to arm yourself and make every partnership secure.
Frequently asked questions
What does third party risk management mean?
Third-party risk management means identifying, assessing, and reducing risks that come from vendors, suppliers, or partners. TPRM helps ensure your business stays safe and protected while working with outside companies.
What are the five stages of third party risk management?
The five stages are due diligence and onboarding, risk assessment, fixing or reducing risks, ongoing monitoring, and finally, offboarding vendors once the relationship ends.
How is TPRM different from GRC?
A third-party risk management framework focuses only on risks from outside vendors and partners. GRC, on the other hand, is a slightly broader concept that covers all of a company’s governance, risks, and compliance.
How do you handle third party risk?
Handling third-party risks is not always easy, but it can be done when you have the right plan. Check vendors often, set clear contracts, monitor them regularly, and create a plan to fix problems if risks arise.
What is an example of a third party risk management framework?
A good example is the NIST Cybersecurity Framework. This helps companies identify, protect, and detect risks. It gives them the ability to respond and recover from risks tied to outside vendors and partners.
How frequently should third-party risks be reviewed?
Most companies review vendors once a year, but high-risk or critical vendors should be checked more often, like every quarter, to stay safe.
What are the best practices for TPRM?
Best practices for TPRM include setting clear rules, having strong vendor partnerships and checks, ongoing monitoring, risk-based contracts, and response planning. For modern businesses, using technology and automation helps save time and manual effort.
How can small companies build an effective TPRM plan with limited staff or budget?
Small companies can build a good third party risk management plan, too. They can focus on their most important vendors, use simple risk checks, and standardize processes so TPRM works without needing big teams or money.
Schedule a Demo
We’d love to hear from you. Please give us a call on +1 315-645-2799.
Explore more from Procol
Discover expert tips, how-to guides, industry insights, and the latest procurement trends.

Procurement orchestration: All you need to know in 2026
Explore the value of procurement orchestration, how it works, its benefits,...

Top 22 spend management KPIs to optimize procurement in 2026
Today’s business world has moved from just ‘buying’ to ‘managing spend’...

What is supplier diversity and why is it important?
In the modern corporate competitive world, where both market resilience and...









