Rutuparna Rout • January 29, 2026
Vendor risk management (VRM): A complete guide 2026

Last update: February 16, 2026

Vendor risk management is important for creating resilient and effective supply chains. Companies rely on other organizations to conduct key operations, which can expose them to the risk of compliance failures, operational delays, financial failure, and reputational damage. Effectively managing vendor risk requires clear strategies, practical tools, and the appropriate functions throughout the organization. In this blog, we discuss key differences, common risks, top strategies, best practices, sustainability links, and how Procol helps streamline vendor and supplier risk management.
What is vendor risk management?
Vendor risk management is the process of identifying, assessing, monitoring, and mitigating potential risks associated with third-party vendors and suppliers, which also include financial instability, non-compliance with regulations, data breaches, operational failures, or sustainability concerns. Implementing risk management practices, businesses can ensure continuity, strengthen supply chain resilience, and protect their reputation. As global supply chains become more complex, vendor and supplier risk management software has become a critical part of long-term business strategy.

Why is vendor risk management important?
Vendor risk management is crucial for modern businesses as organizations increasingly rely on third-party vendors and suppliers for essential products, services, and operations. While outsourcing and partnerships bring efficiency, cost savings, and expertise, they also introduce significant risks that can directly impact performance, compliance, and reputation. Without proper oversight, issues such as vendor bankruptcy, data breaches, supply chain disruptions, or unethical practices can quickly escalate and harm the business.
A strong vendor risk management framework helps identify, assess, and mitigate these potential risks before they affect operations. For instance, checking on a vendor’s financial status ensures that a massive failure does not interrupt the supply. In the same way, assessing cybersecurity practices prevents vendors from becoming a weak entry point for hackers. In regulated next-level industries such as finance or health, vendor risk management also ensures that compliance requirements are adhered to and that the chance of penalties and fines is reduced.
In addition to compliance and protection, vendor risk management creates more robust and transparent partnerships. It guarantees that vendors uphold principles of ethical behavior, environmental sustainability, and quality performance consistent with organizational values. Ultimately, effective vendor risk management protects business continuity while promoting resilience, trust, and sustainability in a highly interconnected business environment.
What are the different types of vendor risks?
Vendor risks can be classified into different categories, such as operational, financial, cyber-security, compliance, reputation, strategic, and geopolitical risks. Businesses will rely on these vendors and suppliers to keep operations running smoothly, however, every vendor relationship poses some amount of risk. It is essential to identify and manage this risk to avoid operational interruptions, lower costs, or protect the reputation of the business.
1. Financial risk
Whenever a supplier or vendor has cash flow, debt, or even goes bankrupt, this can result in an unexpected supply disruption or even unexpected increased costs for the business.
2. Operational risk
When processes are inefficient, when logistics are poor, or when products/services are delivered late, it can cause a disruption in production schedules, impact customer obligations, and in general lower productivity.
3. Legal risks
A vendor who does not comply with regulations, trade laws, or even breaches a contract may lead to fines, litigation, or even suspension of operations. Any violation could have an impact on the parties’ partnership over a long period.
4. Cybersecurity risk
A vendor who has access to a company’s data or systems, and is unaware of a breach or hacking or data leaks, could expose companies to risk when they fail to use reasonable security measures.
5. Quality risk
Receiving low-quality raw materials, defective products, or inconsistent service can result in damaging customer confidence in services or products, leading to increased costs of rework and ultimately affecting brand name potential.
6. Reputational risks
Partnering with suppliers or vendors involved in unethical practices, such as labor exploitation or environmental violations, can severely tarnish the company’s public image.
By proactively addressing these risks, businesses can build stronger, more resilient supply chains that ensure continuity, compliance, and long-term growth.
Difference between vendor risk management and vendor management
Vendor Risk Management (VRM) is a component of vendor management, and effective vendor management will include a solid VRM program. It is also important to mention that VRM is not the same as third-party risk management. Vendor risk management and vendor management often overlap but differ in focus.
| Vendor risk management | Vendor management |
|---|---|
| Focuses on risks linked to third-party service providers, contractors, and technology partners. | Concentrates on identifying, assessing, and mitigating risks associated with vendors. |
| Common risks include data breaches, compliance failures, intellectual property misuse, and service delivery issues. | Activities include contract negotiation, performance evaluation, cost management, and collaboration. |
| Managed using compliance tools, cybersecurity solutions, and performance monitoring systems. | Managed using vendor management systems, performance scorecards, and communication tools. |
| The approach emphasizes safeguarding data, compliance, and service performance. | Emphasizes efficiency, quality improvement, and the value of long-term partnerships. |
| Examples: IT services, consultants, cloud providers, and logistics partners. | Examples: raw material suppliers, manufacturing partners, service contractors, and maintenance providers. |
In short, vendor management drives operational efficiency and strong vendor partnerships, while vendor risk assessment protects the organization from vulnerabilities and disruptions. Businesses need both approaches to achieve sustainable growth and resilience in today’s interconnected environment.
Top strategies to manage vendor and supplier risks
The leading tactics for vendor and supplier risk management software are to exercise strategic selection and due diligence for new and existing vendors, create a clear contractual basis with Service Level Agreements (SLAs), monitor vendor performance and cybersecurity continuously, develop contingency and incident response plans, and maintain strong relationships with key suppliers.
1. Conduct thorough due diligence
Before onboarding, evaluate vendors and suppliers on financial stability, compliance history, reputation, and operational capabilities. This helps identify potential risks early and ensures only reliable partners are chosen.
2. Segment and prioritize suppliers
Not all suppliers or vendors carry the same level of risk. Categorizing them based on criticality, dependency, and impact allows businesses to focus risk management efforts where they matter most.
3. Implement strong contracts and SLAs
Clearly define service-level agreements, compliance requirements, performance metrics, and penalties in contracts. Well-structured agreements set expectations and reduce the chance of disputes.
4. Continuously monitor your performance
Keep track of your vendors’ and suppliers’ performance through scorecards, audits, and real-time monitoring solutions. Ongoing review signals warning signs and stops minor issues from growing into major risks.
5. Utilize technology and automation
Vendor risk management applications allow businesses to centralize information, automate monitoring and flagging of risks in real-time, and ensure compliance with minimal human intervention.
6. Create contingency and backup plans
Ensuring that you have back-up suppliers or safety stock or back-up vendors, in case one of your partners fails to deliver, will provide for continuity of business operations. This minimizes reliance risk while strengthening the overall resilience of the supply chain.
In this way, by leveraging thorough assessments, technology, and proactive planning, organizations can minimize vulnerabilities and create a strong structure surrounding vendor and supplier risk management.
Benefits of effective vendor risk management
Proper vendor risk management software (VRM) provides benefits like cost savings, reduced financial and operational risks, increased security and protection of data, improved business continuity and resilience, and improved requirements for regulatory compliance.
1. Enhanced business continuity
Proactive risk management mitigates disruptions stemming from financial instability, delays, or compliance issues, facilitating smoother operations and an uninterrupted supply chain.
2. Cost savings and improved efficiency
By identifying areas of wastage, primarily through the elimination of quality issues or penalties, businesses can unlock cost savings through improved procurement.
3. Better compliance and greater governance
Strong monitoring mitigates the risk of vendors and suppliers falling short on regulatory compliance, contract adherence, and appropriate industry standards in delivering goods or services so the business avoids penalties or legal action.
4. Improved supplier relationships
Transparent risk management encourages trust, collaboration, and accountability between vendors and suppliers, leading to stronger partnerships based on transparency and collaborative risk mitigation.
5. Protected brand reputation
Risk management provides the protection against poor behaviours, such as unethical practices or data breaches, that can harm a company’s reputation and erode trust in customers.
6. Increased resilience and adaptability
By having contingency plans and a diversified sourcing strategy, the business can react effectively to resilience, whether it is due to increased volatility in the market or geopolitical concerns, or due to natural disasters.
Meaningful vendor and supplier risk management reduces vulnerability while significantly increasing overall competitiveness and long-term sustainable growth in businesses.
Top 10 best vendor risk management tools and software
Vendor risk management tools are essential for identifying, monitoring, and mitigating risks from third-party vendors and partners. They help businesses stay compliant, protect data, and ensure smooth operations. Some of the best tools include:
| Title | Description |
|---|---|
| Procol | Procol differentiates itself as a pioneering vendor risk assessment solution that moves past-dashboard style ratings of risk, embedding risk controls throughout the procurement lifecycle. Whereas cyber rating solutions traditionally only evaluate external signals. Real-time alerts and constant assessment ensure that vendor risks are flagged before they impact business activity. Moreover, Procol’s integrated vendor risk management platform connects sourcing, contracts, and supplier performance to present the user with complete visibility. |
| OneTrust Vendorpedia | Provides complete vendor lifecycle management, covering onboarding, due diligence, compliance, and ESG monitoring. |
| ProcessUnity | Automates vendor risk assessments and workflows with strong dashboards, ideal for regulated industries. |
| UpGuard | Specializes in cybersecurity risk, offering real-time monitoring of vendors’ security posture and alerts for vulnerabilities. |
| Scrut Automation | A modern, agile platform with real-time visibility, customizable questionnaires, and simplified onboarding for fast-growing businesses. |
| PwC India Third-Party Risk Protect | A region-specific tool that manages the full vendor lifecycle while addressing India’s regulatory and compliance requirements. |
| BitSight | Continuously assesses the risk of vendors based on external signals of security, such as indications of malware infections and bot activity. Provides security ratings on a 250 to 900 scale that are intuitive and help organizations benchmark vendor risk. Growing in popularity with enterprises seeking visibility and reporting into third-party cyber risk. |
| SecurityScorecard | Computes scores based on an A to F grade on 12 risk factors such as IP reputation, application security, and leaked credentials. Provides continuous monitoring as well as supporting complexity in the remediation workflow. Great option for organizations looking for external risk intelligence and transparency on scores. |
| Prevalent | Combines automated vendor assessments with evidence collection, risk scoring and compliance tracking. Comprehensive coverage on the entire third-party lifecycle, from onboarding to ongoing monitoring. Really good application for enterprises looking for a “single pane of glass” into vendor risk. |
In conclusion, these vendor risk management tools help businesses improve oversight, reduce vulnerabilities, and build stronger vendor relationships. The right choice depends on organizational needs, industry, and level of risk exposure.
Common challenges in vendor risk management
As organizations increasingly depend on third-party vendors for essential services, managing risks across these partnerships has become more complex. Vendor risk management software is critical, but businesses often face multiple challenges that make the process difficult and resource-intensive.
1. Lack of visibility into vendor operations
Many organizations struggle to gain deep insights into vendor processes, security controls, and compliance practices. This lack of transparency makes it difficult to identify hidden risks and evaluate vendors thoroughly.
2. Managing a large vendor base
As businesses scale, they may work with dozens or even hundreds of vendors. Tracking contracts, performance, and risks across such a vast network becomes overwhelming without proper systems or automation.
3. Evolving regulatory requirements
Regulatory standards like GDPR, HIPAA, and ISO certifications are constantly changing. Ensuring that every vendor complies with these updates adds complexity and requires continuous monitoring.
4. Cybersecurity vulnerabilities
Vendors often become entry points for hackers due to weak security measures. A single breach in a vendor’s system can compromise sensitive data and cause severe reputational and financial damage.
5. Inconsistent risk assessments
When different departments or teams use varied methods to evaluate vendors, risk assessments become inconsistent. This creates gaps that weaken overall risk management efforts.
6. Limited resources and expertise
Smaller companies often lack dedicated teams or advanced tools for vendor risk management. As a result, many potential threats remain undetected until they escalate.
7. Fourth-party risks
Vendors rely on their own suppliers and service providers, creating additional layers of exposure. These fourth-party risks are difficult to monitor but can have serious consequences if overlooked.
Vendor risk management is not without its hurdles. Overcoming these challenges requires clear frameworks, the right technology, and continuous collaboration with vendors to build transparency, security, and resilience.
How to build an effective vendor risk management framework
Creating a robust vendor risk management framework enables your organization to meaningfully identify, evaluate, and address risks associated with third-party vendors while ensuring a strong and effective business relationship and compliance.
The following steps provide a unique way of establishing your vendor risk management framework:
1. Define objectives and scope
Begin with a clear definition of your VRM program objectives. Identify the types of vendors that meet the objectives, the risk domains (cybersecurity, financial, regulatory, operational, ESG) that are included, and the level of criticality.
2. Establish vendor classification and risk tiering
Establish vendor classifications or categories based on the potential impact to your operations, access to sensitive data, and level of risk. Vendors identified as higher risk will require additional monitoring and assessment.
3. Develop standardized risk assessment processes
Develop standardized questionnaires, audits, and evaluation criteria to assess vendor risks under each of the risk domains. Implementing a standardization for all vendors will ensure the same approach is deployed to assess vendors.
4. Provide monitoring and performance tracking
Use dashboards, alerts, and periodic review to identify and continuously monitor vendor performance compliance and potential risks. Continuous monitoring and performance tracking will allow you to identify potential issues before they become problematic.
5. Identify risk mitigation plans
Create clear and defined arbitrating plans for the risks identified with each vendor, including your remediation plan, potential mitigation contract clauses, and contingency plans if the vendor does not meet your expectations.
6. Set clear roles and responsibilities
Assign internal teams such as procurement, IT, compliance, and legal to oversee vendor risk and maintain documentation.
7. Utilize technology and tools
Consider vendor risk management (VRM) software to facilitate assessments through automated monitoring and streamlined vendor information. Using tools to enhance efficiency can also help with monitoring vendors in real-time.
8. Implement regular reviews and updates to the framework
The landscape of vendor risk will change over time. It is important to regularly review your framework, update risk criteria, and incorporate lessons learned from vendor incidents.
In summary, a strong vendor risk management framework establishes clear policies and processes, consistently measures risk, includes an ongoing monitoring process, and engages collaboratively with distinct teams. A good framework protects the organization from financial, operational and reputational risk, while ensuring vendor relationships are reliable and compliant.
How to create a third-party or vendor risk management checklist
When developing a vendor risk management checklist, begin by identifying and categorizing vendors by risk level. Next, establish your risk assessment criteria by focusing on financial stability, regulatory compliance, data security, business continuity, and terms of service. For high-risk vendors, evidence should be gathered through questionnaires and reviewing documentation, and you will need to create processes for risk monitoring, remediation, and a documented exit strategy.
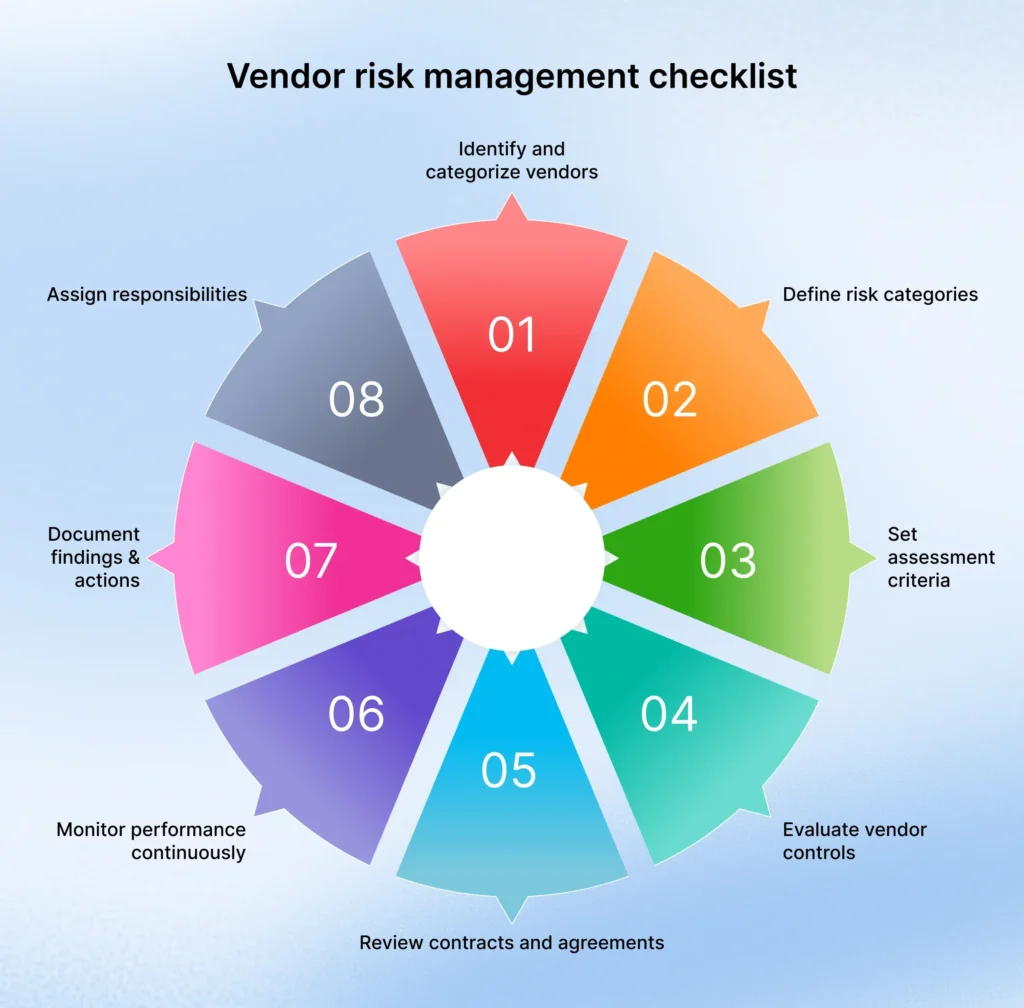
1. Identify and categorize vendors
You should create a list of all vendors and categorize them according to their criticality, access to sensitive data, and risk potential.
2. Define risk categories
Define risk categories, including but not limited to: Cybersecurity, Compliance with laws, Financial stability, Operational performance and performance capabilities, Legal exposure, and ESG/Sustainability Risks.
3. Define assessment criteria
For each risk category, define assessment criteria or checkpoints. For example, for cybersecurity risk you may look at security certifications, audit history, financial statements, and insurance to cover data breaches, regulatory compliance and penalties, and service level agreements.
4. Input risk considerations and evaluate vendor controls
You may also need to confirm the vendor has defined policies, procedures, and other safeguards to respond to each risk area.
5. Review contracts and agreements
It is extremely important to carefully review contracts and agreements to shield your organization from risk. This involves ensuring that the contract contains clearly defined key clauses around confidentiality, data protection, compliance, and vendor obligations. You will also want to include termination clauses and contingency plans, which outline what to do if things start to go badly or the vendor does not deliver what you expected.
6. Continuously track performance
Vendor risk management does not stop after you sign the contract. Periodically scheduled reviews, audits, and ongoing monitoring of the vendor’s performance can help surface any new risk or compliance gap that may develop over time. Having continuous oversight helps ensure that the vendor is maintaining its performance standards and that if there are issues they are caught early and do not escalate.
7. Document findings and actions
It is vital to maintain comprehensive documentation of all assessments, risk ratings, and remediation actions for accountability and transparency. This documentation is a clear record of your efforts to manage vendor risk and will help with audits, internal reviews, or compliance with regulatory bodies. Additionally, comprehensive records help you track progress and improvements over time.
8. Assign accountabilities
Vendor risk management depends on clarity of ownership across teams. Having procurement, legal, IT, and compliance claim ownership over a portion of vendor risk management shows you are overseeing things consistently, and each aspect of vendor risk is managed properly. This collective approach mitigates gaps and better prepares you to coordinate rapid responses to risks as they are identified.
Using a structured checklist allows organizations to perform proactive vendor risk management and compliance while enhancing a trustworthy and secure engagement with the vendor.
Automating vendor risk management with Procol
Organizations can achieve a more agile, transparent, and resilient supply chain through automated vendor risk management using Procol by digitizing and streamlining the entire vendor lifecycle. The interactive supplier portal speeds up and streamlines vendor onboarding by allowing vendors to enter documents, data, and provide compliance information directly to the organization, completing the work that would be done manually with less human effort and errors.
It’s as simple as sending a vendor invite, managing custom instructions on how to onboard, and then tracking the vendor submissions to ensure consistent data completion using the interface. Procol provides a strong risk monitoring system using artificial intelligence-based algorithms to identify and flag vendor risks constantly, all while ensuring businesses are a step ahead of disruptions and compliance failures. The reporting and analytical tools provide configurable data dashboards with insight into supplier performance, risk exposure, and vendor health.
It also seamlessly integrates with an organization’s ERP system to centralize procurement and risk data, thus simplifying collaboration, efficiency, and decision-making across teams and departments.
Ultimately, Procol allows procurement and risk teams to overcome siloed and manual processes and shift the focus to intelligent and scalable vendor risk management. Organizations can maintain continuous monitoring of vendor risks to ensure they’re not only compliant at onboarding but throughout their lifecycle relationship with the vendor.

Conclusion
The automation of vendor risk management allows companies to streamline procurement workflows, improve transparency, and actively oversee their vendor risk when working with a third party. Automation drives efficiency increase while protecting and enhancing supplier relationships, as well as improving resilience, throughout the supply chain. Above all, automation and using a risk-aware, digital approach enable organizations to develop a scalable and nimble approach, ultimately enabling them to remain competitive while protecting mission-critical operations and reducing the risk of operational disruption.
Frequently asked questions
What are the types of vendor risks?
Vendor risks can be categorized into several types, including:
Operational risk: disruptions in service or supply chain issues; financial risk: vendor’s financial instability affecting contracts or deliveries; compliance risk: failure to meet regulatory or contractual obligations; strategic risk: misalignment with business goals or poor vendor performance; reputational risk: negative impact on your brand due to vendor actions; cybersecurity/IT risk: data breaches or IT system vulnerabilities.
What are the 4 types of risk categories?
Vendor risks are generally grouped into four main categories. Operational risk arises from day-to-day business activities, while financial risk is related to potential financial loss or instability. Compliance or regulatory risk occurs when vendors fail to meet legal or regulatory requirements. Finally, reputational or cybersecurity risk can affect a company’s brand image or data security, making it essential to manage vendor relationships proactively.
How can organizations mitigate vendor risks effectively?
Organizations can mitigate vendor risks by conducting thorough risk assessments, monitoring vendor performance regularly, implementing strong contractual safeguards, and ensuring compliance with security and regulatory standards. Using automated VRM tools also helps streamline risk management and maintain business continuity.
Schedule a Demo
We’d love to hear from you. Please give us a call on +1 315-645-2799.
Explore more from Procol
Discover expert tips, how-to guides, industry insights, and the latest procurement trends.

Procurement orchestration: All you need to know in 2026
Explore the value of procurement orchestration, how it works, its benefits,...

Top 22 spend management KPIs to optimize procurement in 2026
Today’s business world has moved from just ‘buying’ to ‘managing spend’...

What is supplier diversity and why is it important?
In the modern corporate competitive world, where both market resilience and...









